
RapidAML Team
2024-06-18
Terrorism is a grave crime against humanity that not only affects property but also millions of lives. Governments across the globe are adopting a ‘Whole-of-Government, Whole-of-Society’ approach for Combating the Financing of Terrorism (CFT).
This article explains the regulatory framework for combating the financing of terrorism across multiple jurisdictions and the CFT compliance measures that businesses and financial institutions are required to follow while addressing the challenges to ensure proper compliance and technological solutions of today and tomorrow that can overcome such challenges.
Financing of Terrorism basically means providing funds or assets to terrorists for their destructive causes. It includes:
Financing of Terrorism takes place through various channels. It involves activities like drug trafficking, extortion, illicit commodities trade, or smuggling. Apart from these illicit ways, FT also includes legitimate routes such as donations, crowdfunding, cultural and religious organisations, and so on.
It is crucial for businesses and financial institutions to understand different methods of FT to prevent the Money Laundering and Financing of Terrorism (ML/FT) risks to their business that can significantly impact the businesses as well as the economy as a whole.
Let’s understand some commonly used methods of Terrorist Financing:
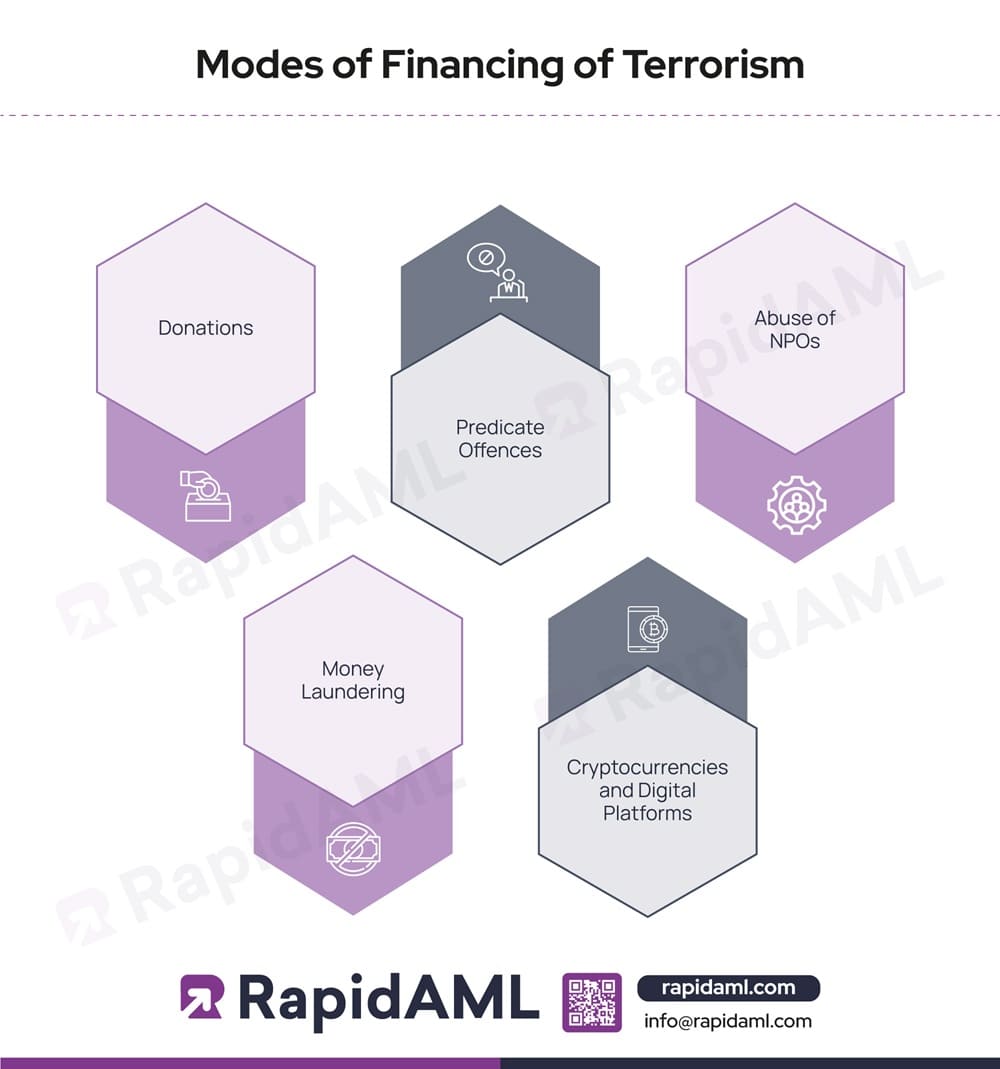
Donations
Donations serve as a significant source of FT through several clandestine methods. Terrorist groups may establish or exploit a legitimate charitable organisation to carry out their fundraising activities.
For instance, an organisation might claim to collect funds under the mask of disaster relief while the funds are being diverted to support terrorist operations. In this case, it becomes difficult to differentiate between genuine help and funds diverted towards terrorism.
Predicate Offences
Terrorist organisations engage in predicate offences to fund their activities. These activities range from drug trafficking to smuggling, robbery, counterfeiting of currency and documents, conducting identity frauds, illicit trade of conflict minerals, oil and gas, and so on.
Abuse of NPOs
Non-profit organisations can sometimes be exploited by terrorists for funding their activities. They abuse NPOs to layer and mask the source and destination of funds. For instance, a donation might be collected in one country and transferred to an NPO in another, and from there, funds are distributed to various terrorist fronts.
Terrorist organisations operate in conflict zones and influence the distribution of humanitarian aid. By doing so, they take away money intended for relief purposes.
Money Laundering
ML and FT often go hand in hand. Terrorists launder large sums of money through structuring or smurfing or by setting up front companies or shell corporations to channel their illicit funds.
Other ML techniques involve using offshore accounts to hide the funds, informal networks, and trade-based ML.
Cryptocurrencies and Gaming Tools
Cryptocurrency trade enables anonymous transactions. The decentralised nature of cryptocurrencies makes them a vulnerable avenue for financial crimes. Terrorists exploit these features to conceal their identities, raise funds, and directly purchase goods and services.
Moreover, terrorists create fraudulent Initial Coin Offerings (ICOs) and use DeFi (decentralised finance) platforms to attract investments from individuals and funnel them into their activities.
Gaming platforms are emerging as the new victims of FT activities. Terrorists purchase, sell, trade, or exchange games or gaming products using fiat money or cryptocurrency. Gaming components such as Graphic Processing Units (GPUs) that render graphics in games, other semiconductor chips and Augmented Reality (AR) and Virtual Reality (VR) are some dual-use goods that terrorist organisations misuse. Furthermore, terrorist organisations leverage the regulatory loopholes for misusing gaming chatbots as messaging systems to coordinate and plan logistical details without being under the radar.
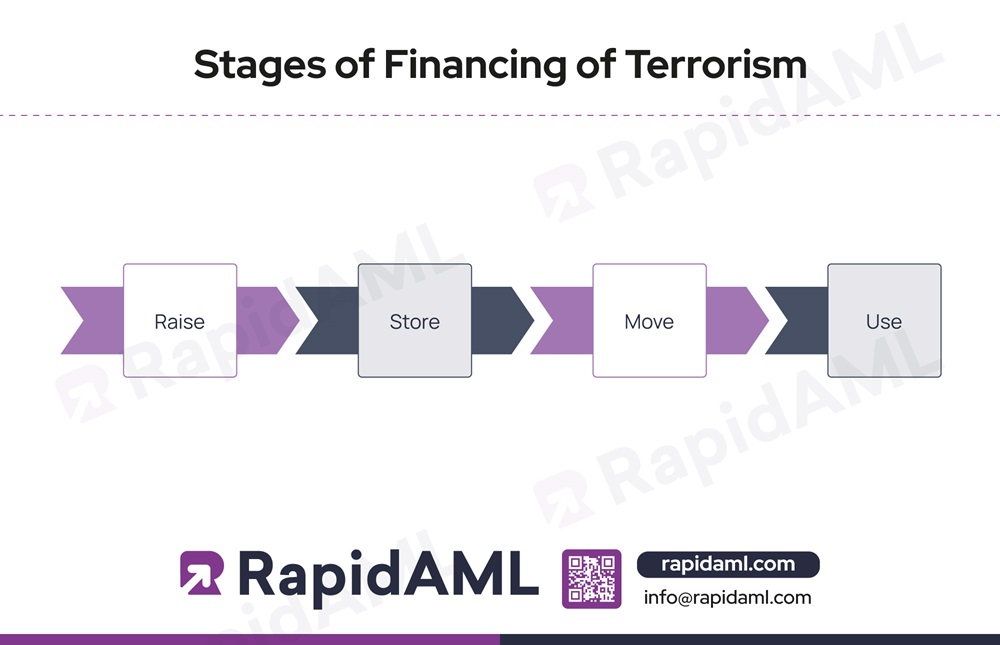
FT happens in 4 stages:
One of the key differences between ML and FT is that in FT, the source of funds may not always be illegal. For instance, terrorists often rely on crowdfunding methods or donations to charities to raise their funds.
The funds raised are then parked through different means before mobilising them for the purpose of conducting terrorist activities, for example, as investments in valuable assets.
The movement stage is where funds are mobilised for the purpose of conducting terrorist activities, such as acquiring arms and ammunition.
Once successfully mobilised, the funds are finally used for their intended purpose of conducting terrorist activities. Businesses and financial institutions are prone to being misused in any of these stages, and hence, they must be proactive in Combating the Financing of Terrorism.
Under the aegis of international organisations, such as the UNSC and FATF, whose role is discussed further in this article, many countries have implemented stringent laws Combating the Financing of Terrorism.
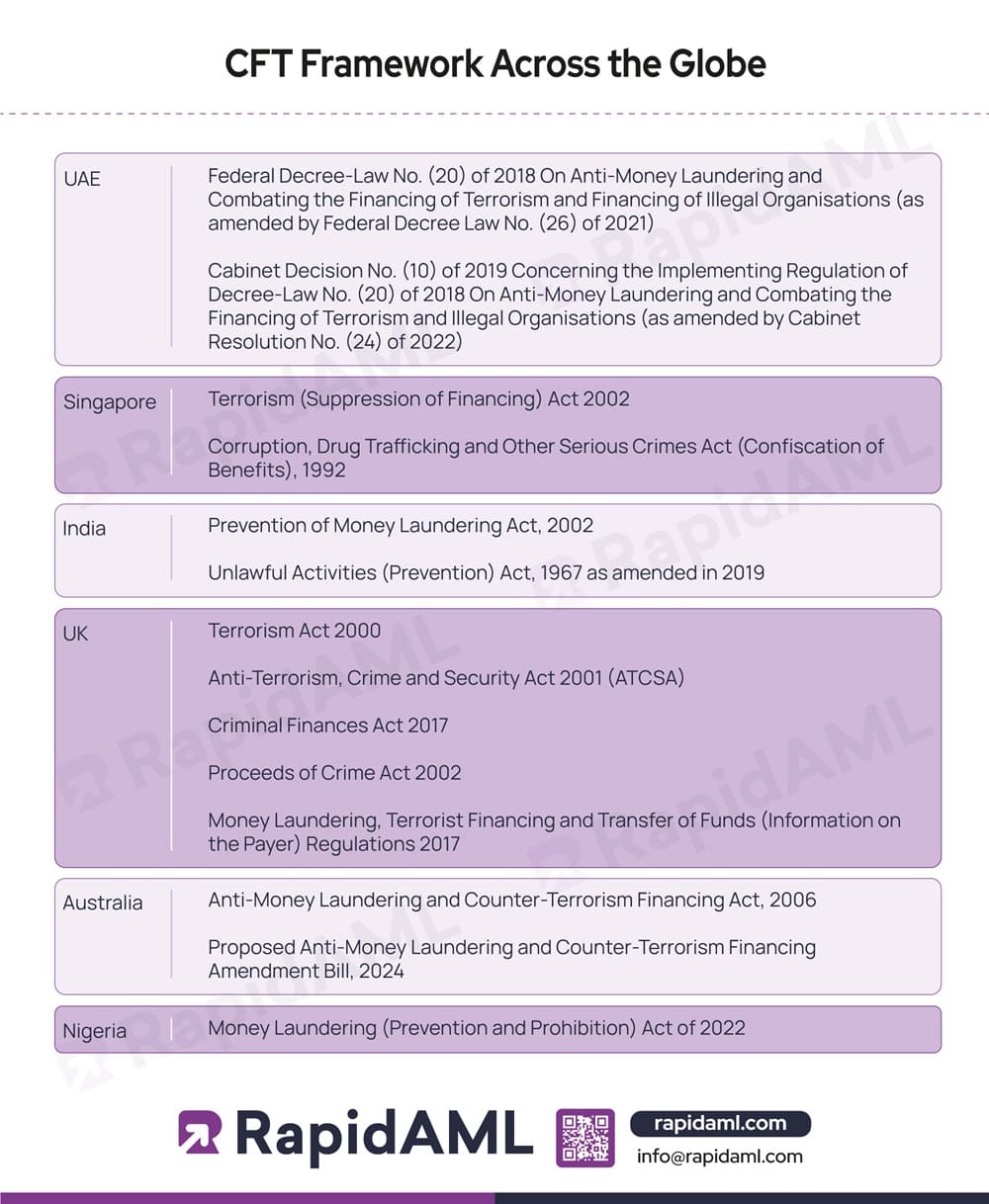
Here is a list of primary legislations implemented by various countries concerning the Financing of Terrorism:
UAE
UAE has implemented the Federal Decree-Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Financing of Illegal Organisations (as amended by Federal Decree Law No. (26) of 2021) and the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree-Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations (as amended by Cabinet Resolution No. (24) of 2022) and corresponding executive regulations and circulars.
Singapore
The Terrorism (Suppression of Financing) Act 2002 and Corruption, Drug Trafficking and Other Serious Crimes Act (Confiscation of Benefits), 1992, are the primary legislations enacted in Singapore concerning CFT.
India
India has enacted the Prevention of Money Laundering Act, 2002, and Unlawful Activities (Prevention) Act, 1967, as amended in 2019, as well as ancillary legislation to prevent the financing of terrorism.
The United Kingdom
The United Kingdom has implemented a series of legislations concerning the financing of terrorism:
Australia currently has the Anti-Money Laundering and Counter-Terrorism Financing Act, 2006, in place dealing with CFT. However, there is a proposed amendment bill referred to as the Anti-Money Laundering and Counter-Terrorism Financing Amendment Bill, 2024, that can transform the AML/CFT regime in Australia.
The Money Laundering (Prevention and Prohibition) Act of 2022 is the main law in Nigeria dealing with CFT.
Businesses and financial institutions are required to comply with CFT norms, including:

Businesses and financial institutions need to identify, evaluate, and understand the FT risks that correspond to the nature and size of their business operations. Businesses and institutions must take the following factors into consideration when weighing their business risk:

Determining the risks associated with the end users of the business’s product or service. Customers who may be connected with adverse media findings pose a high risk to the business and must be assigned a proportionate risk score.
Evaluating the geographical location of the business operations and the customer base. For instance, businesses should determine whether their customer base belongs to or resides in a jurisdiction having weak CFT controls, such as a FATF blacklist or grey list country.
Businesses must assess the susceptibility of the products or services they offer to FT risks. For example, businesses or institutions offering offshore services, their services may be vulnerable to FT risks.
Businesses must consider whether there is unnecessary involvement of third parties, such as agents or distributors, in the delivery channel.
The value, volume, and complexity of transactions are important risk factors that businesses must take into account when conducting risk assessment.
The EWRA/BRA helps businesses and institutions draft clear internal policies, procedures, and controls that can help them prevent FT risks.
Businesses and Institutions must define and document internal policies and procedures for risk management and compliance to support their AML/CFT program. The policy and procedures must include the following components:
Businesses and financial institutions must undertake CDD measures at the time of:
Know Your Customer
As a part of the CFT regulatory framework, it is mandatory to implement KYC procedures as a part of Customer Due Diligence. Businesses and institutions must identify and verify the customer’s identity against independent, reliable source documents, information, and data sources. The KYC process must also be applied to the beneficial owners of the customer, where the customer is a legal entity.
Screening Against the Targeted Financial Sanctions and Adverse Media
Targeted Financial Sanctions (TFS) are aimed at specific natural or legal entities that restrict them from making any transactions. It is like a financial blockade that cuts off the flow of money to terrorist organisations.
National and international regulatory bodies such as the UN Security Council levy financial sanctions that guide the global adoption and implementation of such sanctions. Targeted Financial Sanctions are imposed to disrupt the fund flow through asset freezing or denying access to financial services. TFS also aid intelligence units and law enforcement in locating the financial network of terrorists.
Hence, businesses and institutions must screen their customers against the following lists before establishing business relationships with the customer:
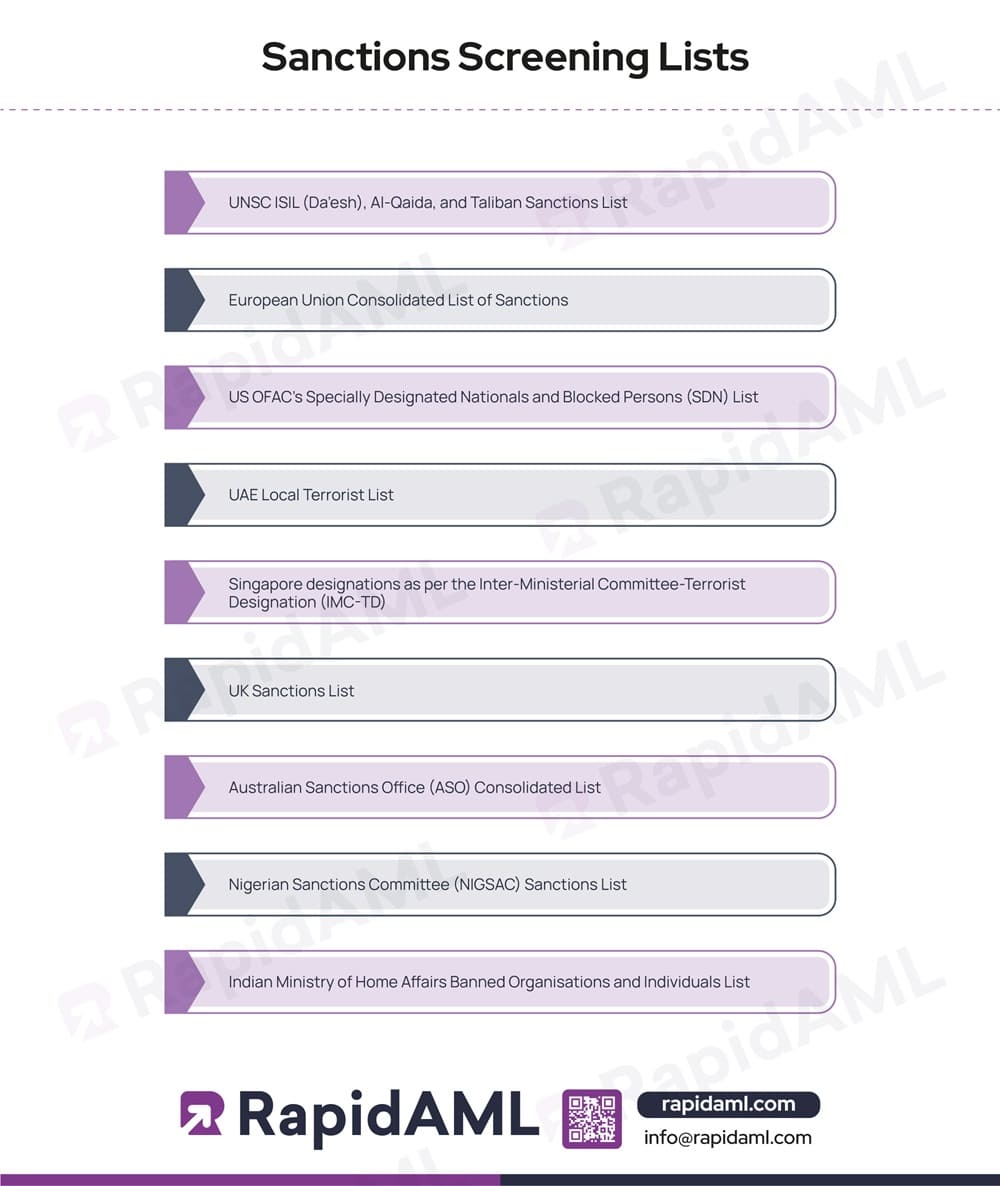
The above-mentioned list of sanctions is not exhaustive. Businesses and financial institutions can screen their customers against other local lists as well to determine their risk profile.
Business must additionally screen their customers against negative news and information to further reduce the risk of FT.
Businesses and institutions are required to terminate business relationships with the customer if their name matches the sanctions list and report to the Financial Intelligence Unit (FIU).
Customer Risk Assessment
Based on the KYC and screening process, businesses and institutions must be able to determine the risk profile of their customers and classify them into high-risk, medium-risk or low-risk customers. For instance, if there are adverse media findings against a customer, then they should be treated as a high-risk customer during the customer risk assessment.
Businesses and institutions must then apply a risk-based approach to due diligence measures, i.e., Enhanced Due Diligence when dealing with high-risk customers. Standard Due Diligence must be applied for a medium-risk customer, and Standard/Simplified Due Diligence can be applied for a low-risk customer.
Enhanced Due Diligence (EDD)
When dealing with high-risk customers, businesses and institutions must apply additional controls as a part of EDD, such as:
The decision to onboard and engage with a high-risk customer must be made with the approval of senior management.
Post onboarding, businesses and financial institutions must monitor the business relationship and transactions with the client on an ongoing basis to prevent FT risks by identifying and reporting suspicious activities or transactions.
However, the reporting requirements vary from country to country. The common elements of reporting a suspicious activity or transactions involve:
Reporting is a regulatory requirement across various jurisdictions where non-compliance with the same attracts penal actions. Thus, it is important for businesses and financial institutions to be aware of their reporting requirements and effectively train their employees and staff members about the same.
Employee training and awareness programs equip employees with the knowledge and skills required to identify and report suspicious activities. Well-trained employees become the First Line of Defence against terrorist financing. Continuous learning ensures that employees are aware of both existing threats and new and evolving tactics. Moreover, it fosters a culture of vigilance and responsibility within the organisation.
Businesses and institutions must train:
The training should include not only the regulatory framework but also the background and context of implementing CFT laws and regulations, the internal policies of the business or institution, and the CFT obligations of the trainees.
Simply establishing an AML/CFT program is not the goal of combating the financing of terrorism. Hence, businesses and institutions should also periodically evaluate the effectiveness of the program through an independent audit mechanism. The objective of an independent audit must be to:
Businesses and institutions are required to maintain all the records of their business relationship for such periods as may be prescribed by the regulatory authorities. These records include:
The importance of fighting Terrorist Financing extends beyond regulatory requirements. Terrorist groups commit acts of violence to instil fear to achieve their political, ideological, or religious goals. Combating the financing of terrorism is important for several reasons:
International regulatory bodies play a key role in the fight against terrorist financing by establishing standards that transcend national borders. These frameworks ensure that every country adopts a collaborative and coordinated approach to detect, prevent, and dismantle the financial flows that support terrorist activities.
International regulatory bodies such as the Financial Action Task Force (FATF) and the United Nations Security Council (UNSC) are continuously working to combat the financing of terrorism (CFT).
The FATF expanded its efforts to combat terrorist financing in 2001. It sets forth international standards for assessing compliance and promoting effective implementation of legal, regulatory, and operational measures
The FATF has published a comprehensive set of 40 recommendations, which are recognised as international standards for combating money laundering and terrorist financing.
The role of FATF is to regularly review and assess member countries’ compliance with FATF Recommendations. FATF puts efforts into fostering international cooperation to combat terrorist funding through its global network of FATF-style regional bodies, such as the Asia/Pacific Group on Money Laundering (AGP) and the Middle East and North Africa Financial Action Task Force (MENAFATF).
By promoting strong legal and regulatory measures, FATF has played a crucial role in shaping global policies and practices and protecting international security and stability.
The UNSC, through the adoption of binding resolutions, establishes international regulatory requirements for member states. They facilitate the identification and freezing of terrorist assets, penalise those involved in terrorist financing and promote international cooperation and coordination.
The UNSC adopts resolutions under Chapter VII of the UN charter, requiring countries to take specific actions to combat terrorist funding, such as travel bans and arms embargoes against these designated individuals and entities.
The UNSC designates individuals and entities involved in terrorist funding through its sanctions committees. Key UNSC regulations include:
These resolutions and their successor resolutions mandate the member states to prevent terrorist financing by freezing assets, targeting FT and PF, and enhancing border controls.
Overall, the UNSC plays a significant role in establishing and implementing stringent legal framework ensuring compliance with international standards to disrupt terrorist financing and enhance global security.
Combating terrorist funding by disrupting the flow of funds is a multifaceted challenge. There are various aspects to it. Here are some key challenges that businesses and financial institutions face in combating the financing of terrorism:
Evolving FT Methodologies
The evolving nature of terrorist funding brings a challenge to efforts aimed at disrupting their funding sources. Terrorists continuously try to exploit loopholes. They diversify their funding sources using legitimate channels like donations and charity and exploit illegal channels. Moreover, decentralised financing networks such as cryptocurrencies add to the complexity.
Exploitation of Technology
Terrorists use encrypted communication platforms to conduct anonymous financial transactions. The borderless nature of the internet makes it difficult to track and disrupt terrorist fund flows.
Misuse of NPOs
Terrorists misuse NPOs to funnel their illicit funds by leveraging the trust and goodwill of these organisations. Funds meant for humanitarian aid are diverted to support terrorist activities, making it difficult to differentiate between genuine and illicit fund flow.
Resource Constraints
Small businesses and institutions may not have adequate resources in terms of technological tools or skilled personnel to implement CFT measures effectively.

The future of CFT lies in embracing technological advancements. Advanced Software solutions such as:
These solutions can help businesses and institutions enhance the following:
In a timely, comprehensive, and cost-effective manner.
Conclusion
Combating the Financing of Terrorism is not just a regulatory but also a moral obligation for all businesses and institutions. This article summarises the practical measures that they can take to ensure effective mitigation of the FT risks.
Dipali is an Associate member of ICSI and has a Bachelor’s in Commerce and a General Law degree.
She currently assists clients by advising and helping them navigate the legal and regulatory challenges of Anti-Money Laundering Law. She also helps companies develop, implement, and maintain effective AML/CFT and sanctions programs.
She knows Anti-money laundering rules and regulations prevailing in GCC countries and specializes in Enterprise-wide risk assessment, Customer Due-diligence, and Risk assessment.
Join our Waitlist