
RapidAML Team
2024-06-18
The regulated entities in UAE are mandated to report all suspicious activities and transactions with the FIU’s goAML portal. It’s important for businesses to identify and report such suspicious transactions on a timely basis and report them without any delay to counter money laundering and terrorist financing. Here is an ultimate guide to investigating suspicious transactions.
Any transaction with or routed through a regulated entity that indicates potential involvement or element of Money Laundering, Terrorism Financing, and Proliferation Financing (ML, FT, and PF) activities either directly or indirectly is known as a suspicious transaction.
According to the Central Bank of UAE (CBUAE) and in alignment with the Anti-Money Laundering and Counter Financing of Terrorism Laws in UAE, a transaction, whether attempted or concluded or customer funds can be referred to as a suspicious transaction for which the regulated entity has reasonable grounds to suspect that the said transaction could potentially be:
A suspicious transaction is not necessarily a transaction that has been concluded. All transactions, be it ongoing, proposed, or executed in the past, irrespective of their completion stage, when found during review or assessment that there exists reasonable ground for suspicion, can be interpreted and must be reported as a suspicious transaction through the goAML portal.
What Does the Term “Reasonable Grounds” Mean?
Reasonable grounds refer to considering the entire situation as a whole with all the facts and evidence available to arrive at a conclusion or decision that any reasonable person would. A reasonable person, also known as a prudent person, is a person who exhibits skill, competence, care, and judgment that aligns with any average person in a society.
It is important to note that regulated entities need not obtain or collect and verify evidence to support filing a suspicious transaction report, as having reasonable grounds to suspect involvement of illicit proceeds through any of the abovementioned indicators and relevant requirements is sufficient.
Routine business transactions and suspicious transactions may, at first glance, look alike. However, they vary distinctly when looked at with a scrutinising keen eye that usually a competent transaction monitoring analyst, risk analyst, AML Compliance Officer (CO), or Money Laundering Reporting Officer (MLRO) possesses.
A suspicious transaction differs from routine business transactions in many ways, such as:
The list of differences among routine business transactions and suspicious transactions indicating potential involvement of ML, FT, and PF activities can stretch quite far. However, what can be summarised as key points of distinction between suspicious and routine transactions is the said transaction’s alignment with the customer’s risk profile and rating assigned. For a suspicious transaction, the nature of the transaction would be inconsistent with the customer’s financial standing and their usual or expected pattern of conducting business.
Business to business and sector to sector, red flags and typologies of suspicious transactions differ. Regulated entities must take into consideration and include in their AML/CFT policies and procedures a list of commonly faced red flags and typologies pertaining to their specific business derived from well-crafted Enterprise-Wide Risk Assessment (EWRA). Here’s a list of a few generalised red flags or typologies of suspicious transactions in UAE:
Some examples of suspicious transactions that regulated entities must be aware of are as follows:
The suspicious nature of a transaction or fund can be interpreted or indicated by comparing or monitoring customer profile indicators such as:
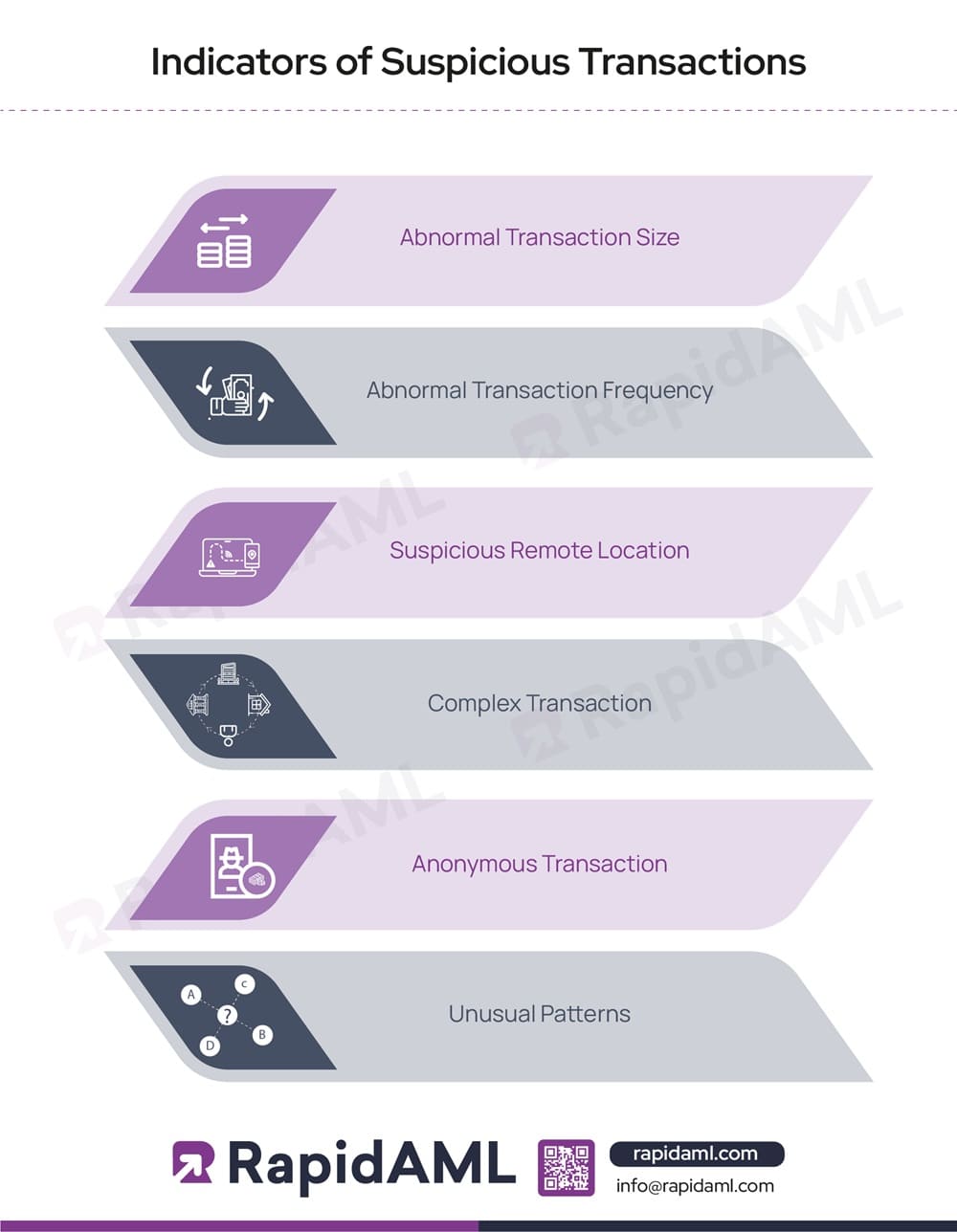
Abnormal Transaction Size: The size or volume of the transaction is found to be abnormal or unusual when compared with the customer information collected during CDD and risk rating assigned during ML/FT and PF customer risk assessment.
Abnormal Transaction Frequency: The frequency at which the customer conducts transactions with a regulated entity deviates or differs from their past transaction frequency and is inconsistent with the customer profile.
Suspicious Remote Location: The location from which the customer usually conducts remote transactions is changing frequently or indicates that the location is a grey-listed or blacklisted country or jurisdiction infamous for illicit activities. The location details of a transaction are generally tracked through transaction monitoring software which tracks the IP address and provides geolocation details of a transaction conducted.
Complex Transaction: The transaction shows elements of unnecessary or legally unjustifiable complexity that involves unknown third parties, shell companies, complex ownership structures, or is routed to and from multiple bank accounts without justifiable cause with the purpose of layering and structuring to separate illicit proceeds from predicate offence from which it was generated.
Anonymous Transaction: A major indicator that must arouse suspicion in the minds of the transaction analysts and other AML compliance personnel of the regulated entity is the anonymity factor involved with any transaction where the customer purposefully disguises UBO information or uses virtual assets such as cryptocurrency to transact where the originator and the beneficiary account details can be disguised. The anonymity factor might be indicative of a deeper underlying element of customer or UBOs of legal entity customers being sanctioned or PEPs or having materially significant and relevant adverse media against them.
Unusual Patterns: Any transaction that deviates from the usual transaction pattern of a customer is said to be an unusual transaction. An unusual pattern may indicate the involvement of ML/FT or PF elements. It is equally important to note that not all unusual transactions can be considered suspicious transactions as per the AML/CFT standards, and regulated entities must consider each transaction individually before classifying or categorising such transactions as suspicious transactions.
Regulated entities, in order to curb ML/FT and PF risks, must set an internal investigation framework as a part of their AML/CFT and CPF policies, procedures, and controls where they outline the internal governance structure responsible for identifying, investigating, internally reporting and reporting to regulatory authorities about the suspicious transactions through the use of relevant control measures such as use of software and equipping personnel with adequate knowledge as to their individual roles and responsibilities surrounding suspicious transaction identification, investigation and reporting. The investigation framework for mitigating suspicious transaction risk consists of the following elements:
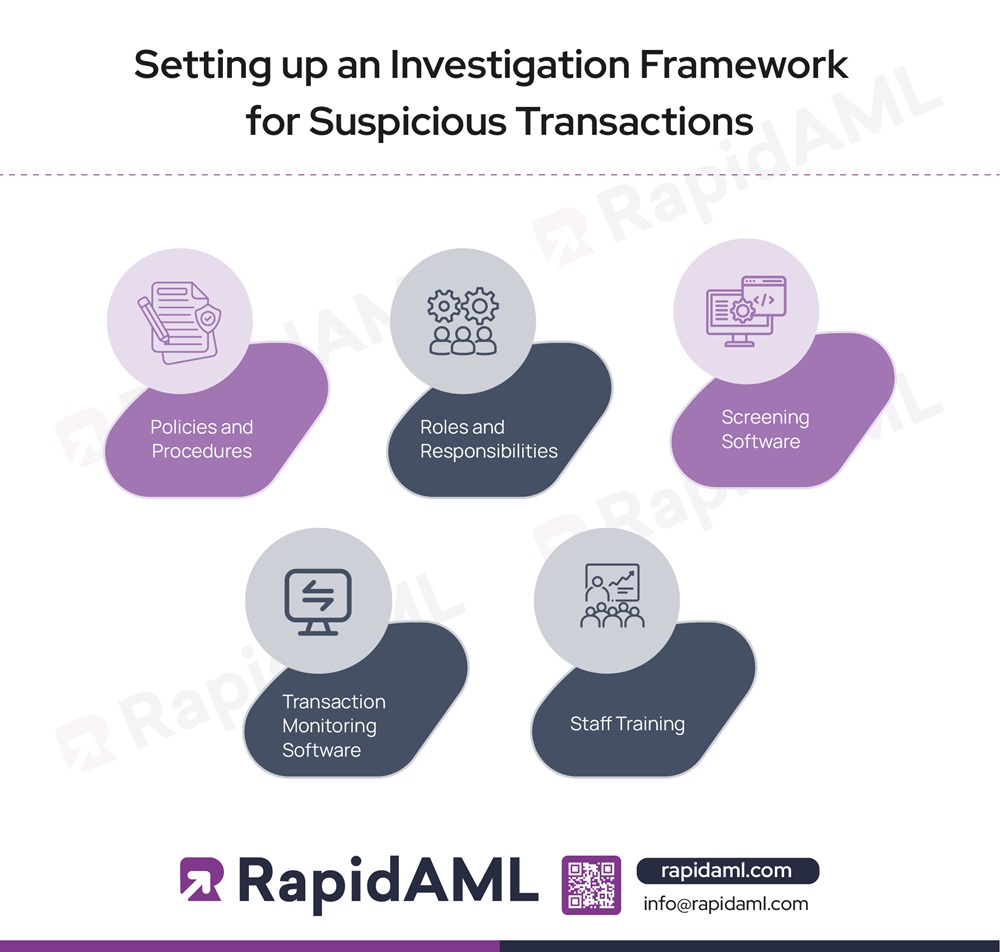
Policies and Procedures: The AML policies and procedures of a regulated entity must outline how the regulated entity and its personnel shall deal with situations where they come across a suspicious transaction. The AML policy of regulated entities must include reference to red-flags and typologies of suspicious transactions that their type and size of business are exposed to.
Roles and Responsibilities: The investigation framework for identifying, investigating, and reporting suspicious transactions forming part of AML policies and procedures must provide for role-specific responsibilities and define workflows across such roles such as that of transaction monitoring analyst, screening analyst, KYC analyst, AML CO or MLRO, and Senior Management. The suspicious transaction investigation framework and AML policies and procedures must be aligned to mitigate the ML/FT and PF risk arising from suspicious transactions.
Screening Software: The suspicious transaction investigation framework must contain clear details as to which screening software the regulated entity intends to rely upon and whether they have conducted an adequate amount of sanctions screening software testing and validation to reduce the incidences of false positives to ensure that their compliance efforts are focused. A screening software helps regulated entities identify whether the natural person or legal entity with whom they are conducting business is sanctioned, PEP, or has any materially relevant adverse media against them which might give them reasonable grounds to suspect that funds or transactions related to that customer might be proceeds of crime supporting M/FT and PF activities.
Transaction Monitoring Software: Transaction monitoring software for a regulated entity is the holy grail that helps them identify, investigate, and report suspicious transactions in real-time based on rules and parameters set during the configuration of the software for use by the regulated entity by the software vendor. Regulated entities must invest in well-adjusted transaction monitoring software and ensure that their suspicious transaction investigation framework contains dedicated software for transaction monitoring.
Staff training: For a suspicious transaction investigation framework to be effective, the personnel of the regulated entity must be adequately and appropriately trained with regard to the following aspects:
Regulated entities must seriously consider relying on suspicious transaction detection and monitoring tools or software. Relying on technology helps regulated entities scale by having compliance measures in place and reducing the element of human error.
Though there is ample variety of suspicious transaction detection and monitoring software in the market, regulated entities must adopt a risk-based approach when selecting a suitable software solution after conducting thorough market research, taking demos from vendors, shortlisting suitable vendors based on the business requirement of the regulated entity and making decision after thorough deliberations.
A regulated entity must have in place, a customised suspicious transactions investigation process. A suspicious transactions investigation process must broadly cover the following aspects:
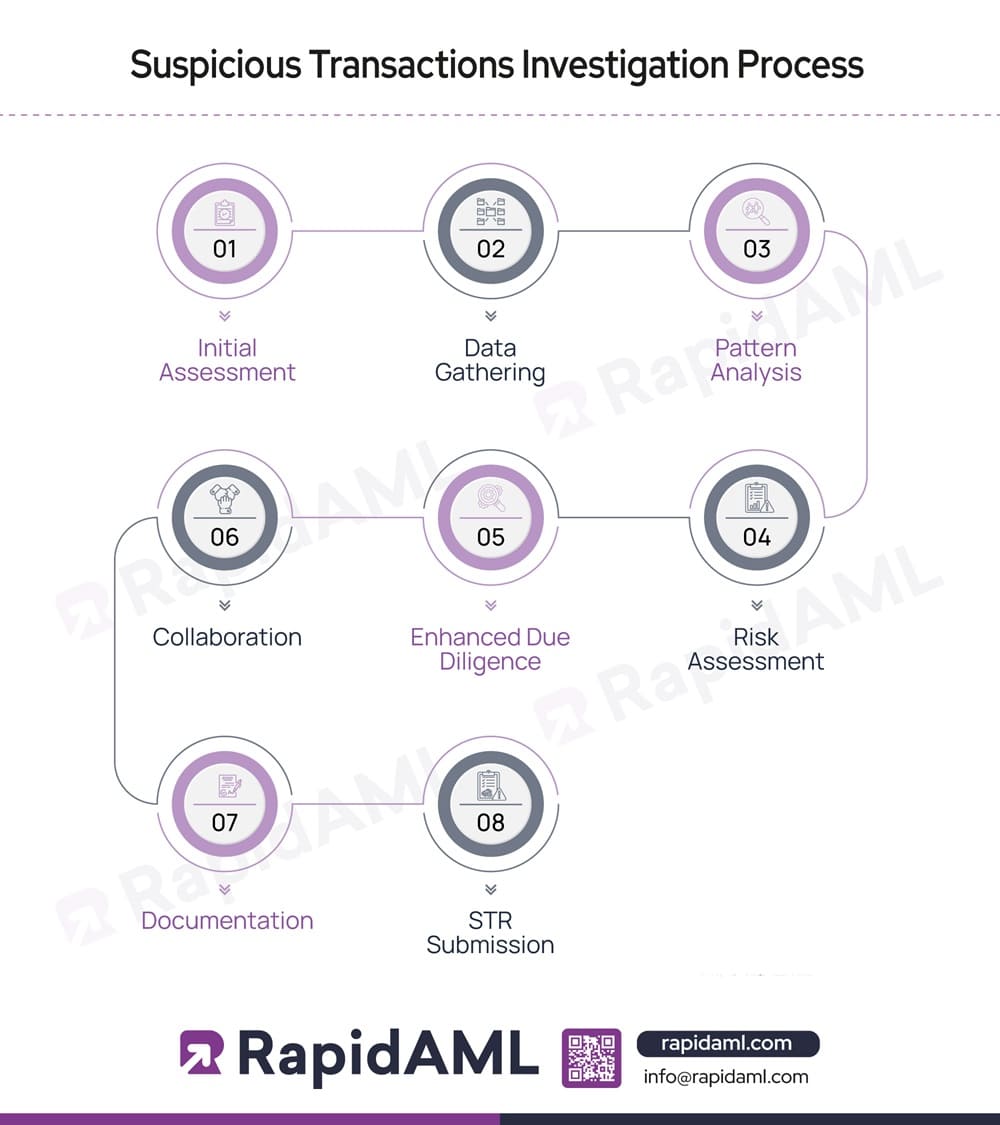
1. Initial Assessment: A regulated entity needs to have in place an internal suspicious transaction identification and investigation process that charts out the red-flags and typologies of suspicious transactions that the regulated entity is vulnerable to. The identification of suspicious transactions is possible through the suspicious transaction identification framework, such as a software through which the personnel gets alerts or notifications based on the parameters set.
2. Data Gathering: The suspicious transaction investigation process must provide for the personnel of the regulated entity to gather as much information or data about the suspicious transaction as practically possible so as to use this data to understand underlying patterns and also use data to fill out Suspicious Transaction Report (STR) narratives for both internal STR reporting as well as to the UAE FIU through the goAML portal.
3. Pattern Analysis: A suspicious transaction investigation process must include measures to conduct pattern analysis so that after gathering information about the suspicious transaction, the transaction monitoring analyst or any other personnel responsible in the regulated entity can look into the transaction history of the customers to see if any pattern emerges that is consistent with typologies and red-flags indicating ML, FT, or PF possibility.
4. Risk Assessment: A regulated entity’s suspicious transaction investigation process should ideally include risk assessment procedures which works in alignment with the guidelines provided by the authorities in UAE.
For instance, after identifying and reporting a transaction as suspicious in nature, the regulated entity should ideally assign high risk rating to such customer and continue or discontinue the business relationship depending on its internal policies and risk-based approach.
5. Enhanced Due Diligence (EDD): A suspicious transaction investigation process must ideally include EDD measures and any other extra measures through which they intend to impose additional control such as seeking additional documents, limiting business activity with such customer, or any such control measures to mitigate the risk from continuing business relationship with such a customer.
6. Collaboration: A suspicious transaction investigation process should provide clear internal policies and procedures with regard to reporting to the FIU through the goAML portal and waiting for response from FIU, the actions it shall take in case no response received, and how it shall cooperate with the FIU if the FIU calls for submitting extra information regarding the transaction.
7. Documentation: A suspicious transaction investigation process must clearly state the methodology, tools, formats, sequence, and checklists for documentation of internal STR process as well as the documentation of STR on the goAML portal.
8. STR Submission: A suspicious transaction investigation process must clearly include steps, timelines, workflow escalation checkpoints, and overall process for STR submission on the goAML portal by the regulated entity.
The UAE AML/CFT law requires the AML Compliance Officers of regulated entities to receive information, assess, analyse, study, and review the information regarding suspicious transactions and decide whether to file STR with FIU or not file STR while continuing business relationship with reasons to not file the STR.
The AML Compliance Officer of the regulated entity must ensure that all the required and necessary measures are taken to ensure that suspicious transaction identification and STR submission process takes place smoothly.
The process of investigation of suspicious transactions comes with its own set of challenges, such as follows:

Inadequate Data: If the information itself about a suspicious transaction is inadequate, such as the:
Then, the results generated during the monitoring of transactions might generate inaccurate results, leading to an unsuccessful investigation due to a lack of adequate information.
False Positives: Another challenge during the investigation is coming across a transaction monitoring alert that is a false positive, meaning that the transaction monitoring system generated an alert but the alert identified a transaction wrongly as a suspicious one.
False Negatives: After false positives, false negatives pose a much grave challenge as this means transactions interpreted as non-suspicious ones might actually be suspicious ones, leading to non-reporting of them and consequent non-compliance and fines.
Encrypted Data: Data about transactions, when encrypted, makes their monitoring tricky as the regulated entity will not be able to identify indicators of suspicion, making it difficult to identify suspicious transactions in a timely manner for further investigation and reporting.
International Transactions: When transactions are conducted across geographical boundaries, multiple factors play their role, such as regulations of the other country involved, mode of transaction, whether the country itself is high-risk, and so on, posing challenges to tracking and monitoring of the transaction.
Resource Availability: Another major factor creating a challenge for suspicious transaction identification and investigation is resource availability. Often, a regulated entity might not be able to invest in a transaction monitoring software, leading to depending on manual input in going through transaction registers to identify anomalies, leading to human errors.
To prevent the occurrence of challenges while investigating suspicious transactions, regulated entities can adopt the following best practices:
Regulated entities are prone to ML/FT and PF risks from their customers, the geographies to which their customers belong, and the mode, timing, frequency, and manner in which the customers execute their transactions. To mitigate the risks emerging from the transaction component, regulated entities must put in place a framework to investigate suspicious transactions and set up an internal process to report them to the FIU through the goAML system.

Purva is a Certified Anti-Money Laundering Specialist (CAMS) and a Lawyer with 5+ years of experience.
She has substantial knowledge of Anti-Money Laundering Laws, Rules, Regulations, and AML Compliance Processes. Purva has been instrumental in drafting RegTech processes, corporate policymaking, and fulfilling various legal research and drafting requirements arising from AML laws and regulatory technology.
Solutions
Transaction Monitoring
Regulatory Reporting
Services
Industries
Lorem Ipsum
Lorem Ipsum
Lorem Ipsum
Lorem Ipsum
Lorem Ipsum
© RapidAML 2025
Solutions
Transaction Monitoring
Regulatory Reporting
Services
AML/CFT Health Check
Industries
Lorem Ipsum
Lorem Ipsum
Lorem Ipsum
Lorem Ipsum
Lorem Ipsum
© RapidAML 2025
Sign Up Form